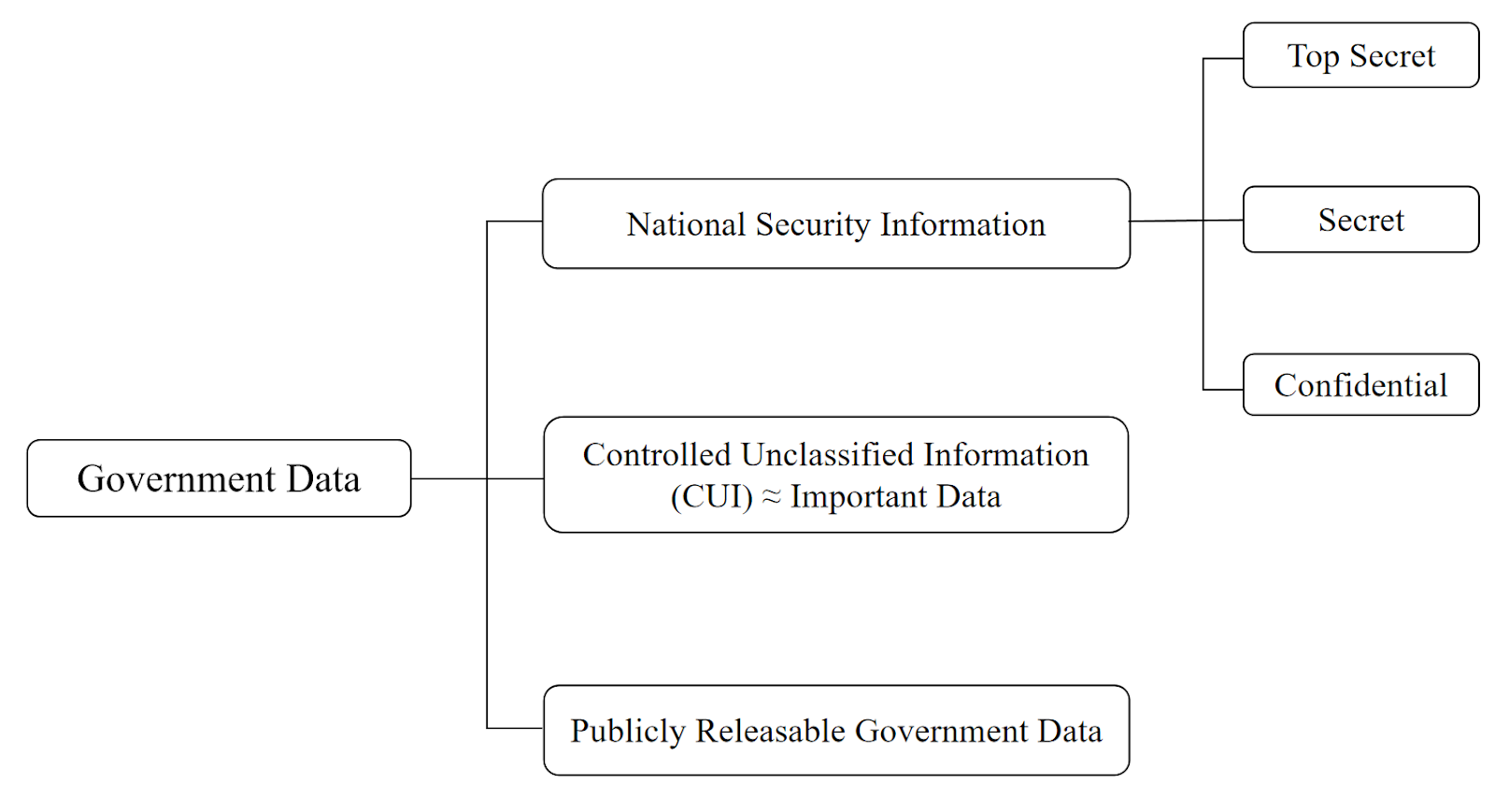
With the rapid development of informatization, how to better safeguard national security in an increasingly complex information environment has become a critical consideration in digital legislation. A key issue within this context is how to identify data, beyond state secrets, that directly impacts national security and to afford such data special protection. Against this backdrop, both China and the United States have established their own sensitive data protection frameworks. Unlike China, which explicitly introduces the concept of “Important Data” in legal instruments such as the Data Security Law, “Important Data” is not a formal term within the U.S. legal system. However, in terms of legislative intent, the concept of “Controlled Unclassified Information” (CUI) within the U.S. legal framework roughly corresponds to “Important Data” in China and serves as a key mechanism for safeguarding national security through data protection.
Ⅰ. “Important Data” vs. “Controlled Unclassified Information”
According to Article 62, Paragraph 4 of the Regulation on the Security Protection of Network Data of China, “Important Data” refers to data that, within specific sectors, specific groups, or specific regions, or when reaching a certain level of precision and scale, may directly endanger national security, economic operations, social stability, public health, or safety if tampered with, damaged, leaked, or illegally acquired or used.
CUI refers to information created or possessed by the U.S. federal government or an authorized entity that does not meet the standards for classification as “National Security Information” under the Executive Order 12958, but if disclosed without authorization, could pose risks to governmental functions, individual privacy, legal proceedings, business confidentiality, and other protected interests.
In 2010, the United States issued the Executive Order 13556 on CUI, requiring federal agencies to implement security protections for CUI in accordance with applicable laws, regulations, and policies, and to manage CUI under a publicly unified institutional framework. In 2016, 32 CFR Part 2002 of the Code of Federal Regulations stipulated the policies for the designation, safeguarding, dissemination, marking, decontrol, and handling of CUI, while also setting out requirements for self-inspection and oversight, thereby providing regulatory guarantees for federal executive agencies and organizations in handling, holding, using, sharing, and receiving CUI.
-
Similarities
On the one hand, both “Important Data” and CUI take the safeguarding of national security and interests as their fundamental legislative value orientation. On the other hand, both fall within the “intermediate level” of the national data security system, constituting sensitive information that lies between state secrets and publicly available data.
-
Differences
First, the scope of the two concepts differs to a certain extent. As defined above, “Important Data” has a broader scope of coverage; aside from government and state-owned enterprises and institutions, other commercial enterprises may also hold such data. In contrast, CUI is, in principle, held by federal government, although it may also be possessed by non-federal entities and private entities through authorization or contractual arrangements. However, it should be noted that the proprietary information of private entities does not fall within the scope of CUI.
In addition, the two differ in legal basis, regulatory authorities, classification standards, and identification methods. These differences are presented in the table below.
Ⅱ. Comparative Analysis of General Compliance Obligations for Enterprises
-
Obligation to Identify: Are Enterprises Required to Proactively Identify Sensitive Data
- Identification of Important Data in China
In China, data controllers are obligated to identify whether the data they handle constitutes “Important Data.” Although relevant regulations require competent authorities to issue “Important Data Catalogs,” the issuance of such catalogs has been slow over the years, and some catalogs contain relatively vague descriptions, making them difficult to implement in practice. As a result, the identification of Important Data has long been a significant challenge for enterprises, raising debates over how to implement this regime and whether enterprises are capable of autonomously identifying “Important Data.”
To address this issue, on the one hand, China has been continuously promoting the formulation of specific Important Data catalogs across various regions and industries; on the other hand, it has issued supplementary regulations to provide enterprises with clearer guidance.
The Provisions on Promoting and Regulating Cross-Border Data Flows, issued by the CAC in March 2024, stipulate that in the context of Important Data outbound transfer declarations, “where data has not been designated or publicly announced as Important Data by relevant authorities or regions, data controllers are not required to submit a security assessment for outbound transfer as Important Data.” Further, on 30 May 2025, the CAC released a Q&A on Cross-Border Data Security Management Policies, clarifying that “if there are no published standards for data classification and grading or rules for the identification and declaration of Important Data within an industry or sector, and data controllers have not been notified by relevant authorities to carry out the identification and declaration of Important Data, the failure to identify or declare Important Data and to provide enhanced protection for such data will not be deemed a violation of Important Data protection requirements, nor will it result in administrative penalties.”
These provisions provide enterprises with more operationally feasible and clear guidance for the identification of Important Data, indicating that data not designated or publicly announced by relevant authorities as Important Data does not need to be managed as Important Data.
- Identification of CUI in the United States
As noted above, unlike China, which requires enterprises to proactively identify Important Data, the United States has issued the CUI Registry as the identification catalog, with the primary responsibility for identification resting with the government. Nevertheless, entrusted enterprises are still required to fulfill certain obligations:
- According to 32 CFR §2002.12 and the NARA Marking Handbook, agencies or enterprises entrusted with handling CUI (such as government contractors, research institutions, or third-party service providers) must first follow federal contracts or guidance to distinguish and manage CUI and non-CUI data when handling CUI. During the classification and identification process, they are prohibited from arbitrarily altering the classification, dissemination restrictions, or marking formats of CUI. In cases of ambiguity, they should proactively confirm with the government project officer (COR).
- Additionally, CUI handlers are obligated to mark CUI appropriately, with the marking divided into three parts separated by double slashes: (a) the designation “CONTROLLED” or “CUI”; (b) the CUI category or subcategory, with the prefix “SP-” if special handling requirements apply; and (c) the dissemination control marking, of which there are currently 10 types, such as “NOFORN” for no foreign dissemination and “FEDONLY” for federal employees only.2 Example marking: CONTROLLED//EXPORTCONTROL//NOFORN.
-
Risk Assessment
Important Data in China: China requires that Important Data undergo a data security risk assessment and that a written report be prepared and retained for inspection before “processing, provision, entrusted processing, joint processing, or cross-border transfer.” Additionally, data controllers must conduct annual risk assessments of their network data processing activities and submit risk assessment reports to competent authorities at or above the provincial level.
CUI in the United States: Similarly, the United States has established technical security standards for handling CUI on non-federal information systems under NIST SP 800-171, which outlines requirements for the risk assessment of the processing, storage, transmission, and disposal of CUI.
-
Security Safeguards
Important Data in China: Important Data controllers are required to establish and improve data security management systems and technical control measures, especially when mergers, divisions, dissolution, or bankruptcy may affect the security of Important Data, in which measures must be taken to ensure network data security. Additionally, data controllers must designate responsible persons and establish management structures for network data security. In specific situations, security background checks should be conducted on responsible persons and personnel in key positions, and relevant personnel training should be strengthened.
CUI in the United States: Similarly, CUI handlers are required to implement 14 categories and 110 control measures under NIST SP 800-171, covering areas such as access control, auditing, configuration management, identity authentication, and data protection, with additional controls applicable to defense contracts. CUI handlers must adopt encryption, isolation, and other measures to securely store CUI on physical media or systems and are prohibited from storing CUI on unapproved cloud services or overseas data centers without federal government approval. Upon project completion, CUI must be destroyed in accordance with NIST SP 800-88 standards. In the event of security incidents such as CUI leakage, intrusion, or loss, relevant handlers must report to the responsible federal agency within 72 hours, initiate emergency response procedures, and isolate affected systems. Subsequently, a detailed incident report and remediation plan must be submitted. Entrusted agencies or enterprises should designate a CUI compliance officer or specialist and conduct regular training for employees on CUI identification, marking, and access management. Internal compliance systems should also be established, such as CUI Handling Procedures and CUI Sharing Approval Systems.
Ⅲ. Comparative Analysis of Cross-Border Data Transfer Management Requirements
- Cross-Border Transfer Requirements for Important Data in China
China imposes strict management requirements on the cross-border transfer of Important Data. According to Article 37 of the Cybersecurity Law, Article 31 of the Data Security Law, and Article 4 of the Measures for Security Assessment of Cross-Border Data Transfer, Important Data, in principle, must be stored within the territory of China. If it is truly necessary to provide such data abroad, a security assessment for cross-border data transfer must be filed with the national cyberspace administration through the local provincial-level cyberspace administration.
In other words, regardless of the type, quantity, or purpose of processing, Important Data in China can only be transferred abroad after passing a security assessment for cross-border data transfer. In practice, regulatory authorities adopt a more cautious approach toward security assessments involving the cross-border transfer of Important Data. As of March 2025, the CAC had completed 298 security assessment filings for cross-border data transfers, among which 44 filings involved Important Data. Of these, 7 applications were rejected, resulting in a rejection rate of 15.9% for Important Data filings.
- Cross-Border Transfer Requirements for CUI in the United States
Unlike Chinese law, which explicitly requires that Important Data may only transfer after passing a security assessment, U.S. law does not have a unified cross-border restriction applicable to all CUI. Instead, cross-border management is implemented through graded control based on applicable national security regulations or sector-specific regulations governing particular CUI subcategories. Generally, CUI subject to outbound restrictions in the United States can be categorized into the following three types:
Export-Controlled CUI: This category requires prior authorization under the Export Administration Regulations (EAR) or the International Traffic in Arms Regulations (ITAR), and contractors are required to establish an Export Control Compliance Program (ECCP).
- CUI Related to National Security and Intelligence Agreements: CUI subcategories such as Intelligence, NATO, and Law Enforcement must not be disseminated to countries or entities lacking sharing agreements or proper authorization.
- Personal Privacy and Healthcare Data: This category is regulated under the Privacy Act of 1974 and the Health Insurance Portability and Accountability Act (HIPAA), among others. If such data is controlled by federal agencies, it cannot be provided to overseas service providers or data controllers without authorization. In specific circumstances, a “cross-border data agreement” must be signed, and federal FedRAMP compliance requirements for cloud service providers may also apply.
For other general categories of CUI, cross-border transfers are relatively less restricted. However, federal compliance clauses typically require that CUI must not be stored or transmitted to cloud services not under U.S. government control or to overseas destinations without prior government authorization.
Ⅳ. Conclusion
Although China’s concept of “Important Data” and the United States’ concept of CUI both focus on safeguarding national security and data security, sharing the same core objective, their management models differ in practice.
In China, the controllers of “Important Data” are primarily enterprises, which collect and hold such data during their business operations, while government authorities supervise and regulate the data processed by these enterprises. Under this framework, greater emphasis is placed on the enterprises’ obligation to ensure autonomous compliance. Enterprises are required to monitor Important Data catalogs, identification guidelines, and related documents in real time, maintain communication with relevant authorities, classify and grade data, and proactively identify Important Data versus general data. Additionally, China imposes strict security management and cross-border transfer controls on controllers of Important Data. The unauthorized cross-border transfer of Important Data without passing a security assessment may result in fines of up to RMB 10 million, revocation of business licenses, and fines of up to RMB 1 million for directly responsible individuals.
By contrast, the U.S. approach to CUI emphasizes federal-level unification, strict classification, clear marking, and industry-specific internal controls. Unlike “Important Data,” which does not distinguish by source, CUI is closely tied to its association with the government, meaning it consists of data owned by the government or collected and used by enterprises under government authorization. The identification of CUI is conducted by the government, while enterprises are responsible for marking and managing CUI based on government requirements. Consequently, enterprises have a clearer expectation regarding which data constitutes CUI compared to Important Data in China. Furthermore, the United States adopts a relatively more relaxed approach to the cross-border management of CUI, imposing controls on only three specific categories of data, thereby providing enterprises with a greater degree of freedom in data processing activities.
In summary, data security has become a focal point of attention globally, but each country has developed its own regulatory requirements for data governance. For enterprises, it is essential to build a layered data compliance framework in the context of globalization, thoroughly understand the data laws and regulations of the jurisdictions in which they operate, and formulate comprehensive and targeted data compliance plans to meet the regulatory requirements of different countries.
Notes List
- CUI Categories,https://www.archives.gov/cui/registry/category-list
- CUI Marking Handbook,https://www.archives.gov/files/cui/20161206-cui-marking-handbook-v1-1.pdf